Traditional CRM typically looks at customers this way: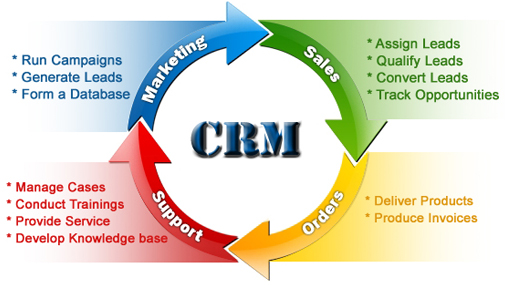 It’s a cycle. One of the reasons we started ProjectVRM is that actual customers are hard to find in the CRM business. We are “leads” for Sales and Marketing, and “cases” for Support. At the Orders stage we are destinations to which products and invoices are delivered. That’s it.
It’s a cycle. One of the reasons we started ProjectVRM is that actual customers are hard to find in the CRM business. We are “leads” for Sales and Marketing, and “cases” for Support. At the Orders stage we are destinations to which products and invoices are delivered. That’s it.
Oracle CRM, however, has a nice twist on this (and thanks to @nitinbadjatia of Oracle for sharing it*):

Here we see the “customer journey” as a path that loops between buying and owning. The blue part — OWN, on the right — is literally the customer’s own space. As the text on the OWN loop shows, the company’s job in that space is to support and serve. As we see here…
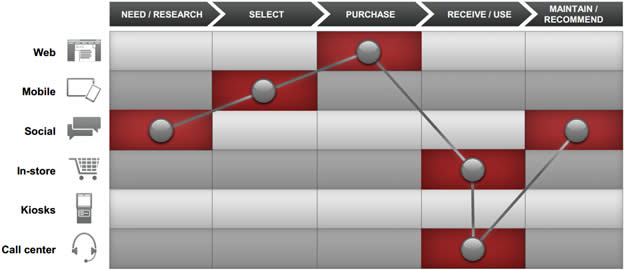
… the place where that happens is typically the call center.
Now let’s look at how this journey looks in our lives, in terms of how much of the time we own stuff and how much of the time we shop for it. The real ratio is closer to this:

And that’s not an exaggeration, since we own everything 100% of the time and shop only a small % of the time.
Now let’s pause to consider the curb weight of “solutions” in the world of interactivity between company and customer today. In the BUY loop of the customer journey, we have:
- All of advertising, which Magna Global expects to pass $.5 trillion this year
- All of CRM, which Gartner pegs at $18b)
- All the rest of marketing, which has too many segments for me to bother looking up
So, in the OWN loop we have a $0 trillion greenfield. This is where VRM started, with personal data lockers, stores, vaults, services and (just in the last few months) clouds.
Now look around your home. What you see is mostly stuff you own. Meaning you’ve bought it already. How about basing your relationships with companies on those things, rather than over on the BUY side of the loop, where you are forced to stand under a Niagara of advertising and sales-pitching, by companies and agencies trying to “target” and “acquire” you. From marketing’s traditional point of view (the headwaters of that Niagara), the OWN loop is where they can “manage” you, “control” you, “own” you and “lock” you in. To see one way this works, check your wallets, purses, glove compartments and kitchen junk drawers for “loyalty” cards that have little if anything to do with genuine loyalty.
But what if the OWN loop actually belonged to the customer, and not to the CRM system? What if you had VRM going there, working together with CRM, at any number of touch points, including the call center?
This is more than a simple dream. One of the coolest things to happen in the VRM development world is this insight, based on actual technology: everything you own can have its own cloud, and each can live inside your personal cloud. Your stuff doesn’t need to have embedded smarts. You can put your things’ smarts inside clouds of their own. Manufacturers can also include clouds along with everything they sell. Inside that cloud can go all the touchpoint contact data required for a genuine relationship, plus useful extras such as service manuals and shortcuts to product updates.
This means the product itself becomes the platform for relationship between the customer and everybody on the sell side, from manufacturer to distributor to retailer to service company. As I explained in this HBR post, that platform — the product’s cloud — is the level table where all those parties sit, at the grace of the customer. Because it’s the customer’s space.
One tablecloth for that platform is the TalkTag.  It’s a simple QR code, like the one on the right. The pioneering company here is Kynetx, through its SquareTag service. It’s a simple way to give anything you have a cloud of its own. Scanning a TalkTag is one way to visit a thing’s cloud, which is also a programmable space. If your thing is lost, you can program it to provide contact information through somebody’s smartphone when they scan it. (Which I have done, and it works.)
It’s a simple QR code, like the one on the right. The pioneering company here is Kynetx, through its SquareTag service. It’s a simple way to give anything you have a cloud of its own. Scanning a TalkTag is one way to visit a thing’s cloud, which is also a programmable space. If your thing is lost, you can program it to provide contact information through somebody’s smartphone when they scan it. (Which I have done, and it works.)
You can also program it to, say, notify the call center when you scan it. For example, I want the TalkTag I just put on my cable modem to notify Time Warner Cable when I scan it. If Time Warner Cable’s CRM system is listening (which should be easy enough to make happen), it can send back a message to my phone, telling me there is an outage in my neighborhood. Or, in the event that there isn’t an outage, the “I’ve been scanned” message from me to Time Warner Cable can jump past stages in the company’s IVR (Interactive Voice Response) system and get me straight to the right person or automated response. That might be, “You need to download new firmware,” or “We have three new service tiers you might want to know about,” or “We see you haven’t paid your bill.”
I have shared this kind of scenario with two call center companies recently, and they liked it a lot. In fact they like the whole idea of VRM systems on the customers’ side that can lighten the burdens of relationship (and open opportunities) for both sides.
The customer journey — his or her experiences of owning and buying — will include more than just interacting with call centers. We use the things we own in countless ways that might be useful to share with others, including the companies that make and sell stuff — and not just through “social” systems like Facebook and Twitter, over which we have little or no control.
We should also be able to integrate data from products that don’t relate but should. In the Quantified Self world, for example, there is a standing need to synthesize data from many devices and databases. This need cannot be solved by asking Nike, Fitbit, Withings, RunKeeper and the rest of them to all make their data un-silo’d and combine-able. And doing it in “social media,” whose only business is advertising at us, won’t work either. We need means of our own.
In the VRM world we’ve been saying the user needs to be the point of integration for his or her own data since Joe Andrieu first expressed that insight in 2007. Now, with personal clouds, in 2013, it’s starting to look possible. In fact the personal cloud, and the whole OWN loop, can also be a platform for intentcasting toward the BUY side.
The OWN side is also where all the privacy technology also sits, chiefly because it is distributed. It is here also that we hold the terms, preferences and policies we express when dealing with companies sitting across the tables set between us.
An interesting case that lies between buying and owning is relationships with service organizations, such as utilities. What we own here is own side of an ongoing relationship. Equipment of our own may be in there, or may not be. Either way, the use of a service — in our homes, cars and pockets — is what we at least control, even if we don’t own it.
So clearly we need a common platform for personal clouds, and for the things we put in them. That platform needs to be small, lightweight, distributed and open source. Right now I see one candidate for that: CloudOS, which is the brainbaby of Phil Windley. (Here’s a search for CloudOS and Windley. Lots of stuff there.) If you’ve got some other hacks, point them out in the comments below.
If we look at the customer experience from the company’s side again, this graphic from Joe Pine and Jim Gilmore does a nice job of framing the possibilities:
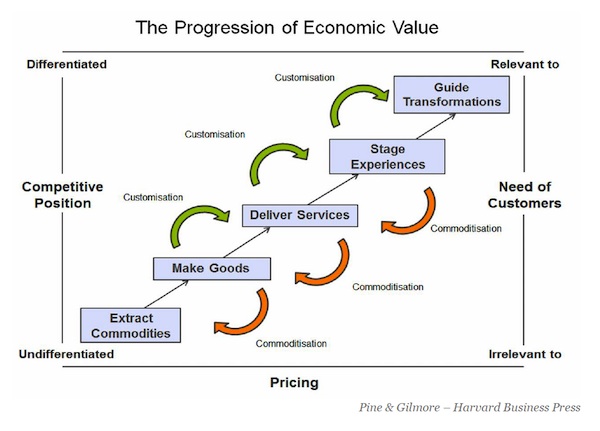
Across the table set in a personal cloud, customers can feed back good intelligence to every one of the loops in that graphic. And, because that data arrives directly and voluntarily, it has far higher quality than inferential data gathered by marketing’s many surveillance methods.
It also re-frames relationship and loyalty, as real things rather than as words marketing recites inside its own echo chambers. It will reduce marketing’s urge to manipulate, and advertising’s urge to personalize in the absence of conscious and voluntary signals welcoming it. The customer journey will thus turn into a virtuous cycle rather than the arduous one it is today.
It can also create a demand chain that can work in tandem with the supply chain, providing far better feedback at every stage. I could go on, but I want to get this up before the latest in the series of Important Calls that punctuate my life. (And they are all Good Things, trust me.)
Bonus link.
* In the comments below the post that follows this one, Ray Wang points to Esteban Kolsky as the original author of this graphic. As I say in my comment below Ray’s, I did hear that from Nitin Badjatia (of Oracle and formerly of Right Now), but I didn’t remember it when I wrote both posts in a hurry. Again, it is the verbs — BUY and OWN — that make the image especially useful for VRM, because they are the customer’s. I don’t yet know if those verbs are Esteban’s or Right Now/Oracle’s. Let me know and I’ll give credit where due.
Save







 It’s a simple QR code, like the one on the right. The pioneering company here is
It’s a simple QR code, like the one on the right. The pioneering company here is 
 The Volt uses
The Volt uses